Patching schedule best practices are the five proven steps IT teams use to keep systems secure and avoid costly downtime: inventory, prioritization, testing, maintenance windows, and verification. According to Gartner, 99% of exploited vulnerabilities are already known at the time of attack. It means organizations that follow these practices prevent most ransomware and outage incidents before they happen.
Why a patching schedule matters
Unpatched systems remain one of the easiest ways for attackers to break in. According to IBM’s Cost of a Data Breach Report 2023, the global average cost of a data breach hit $4.45 million, a 15% increase over the past three years. In the U.S., that number climbs to $9.48 million per breach, with healthcare and finance seeing the highest costs. Many of these breaches last more than half a year before they’re even discovered.
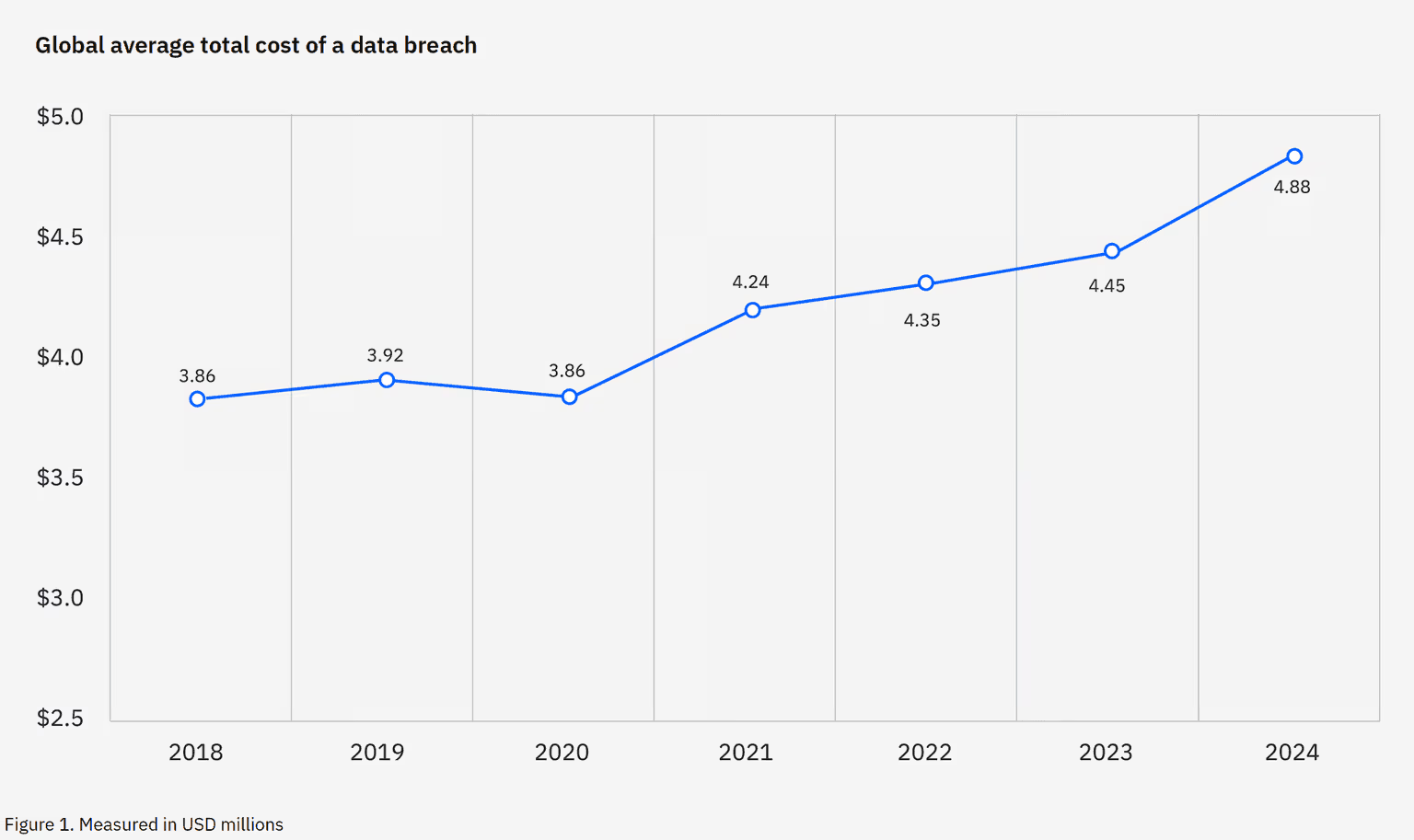
Source: IBM Cost of a Data Breach Report 2024
A single missed update can open the door to ransomware or data theft, while a rushed patch can break a business-critical application. That’s why every IT and security team needs a defined, repeatable patching schedule. The following patching schedule best practices help organizations stay secure while minimizing disruption.
1. Keep a Real-Time Inventory of Assets
A patching schedule is only as strong as the systems it covers. CISA notes that incomplete or outdated asset inventories are one of the main reasons organizations miss critical patches. Blind spots give attackers easy entry points.
To build a reliable inventory, focus on three essentials:
- Track every type of system — servers, laptops, mobile devices, cloud workloads, and containers.
- Use automated discovery tools to ensure new or forgotten assets are identified quickly.
- Organize assets by business importance and exposure level to make patch prioritization more effective.
Using Microsoft 365’s built-in tools, like Microsoft Intune for device management, and Microsoft Defender for Endpoint for automated asset discovery, can provide real-time insights across both cloud and on-premises environments. By integrating with Entra ID (formerly Azure AD), dynamic tracking of user and device identities will enable precise patch targeting and policy enforcement.
Summary: without a real-time inventory, patching schedules leave critical systems exposed.
2. Prioritize Patches Based on Risk
Not every patch is equally urgent. Verizon’s Data Breach Investigations Report shows attackers repeatedly exploit a small set of known vulnerabilities that remain unpatched in the wild. That’s why one of the most important patching schedule best practices is to prioritize based on real-world risk rather than treating every update the same.
Effective prioritization means:
- Threat intelligence: Combine CVSS scores with exploit data.
- Exposure: Patch internet-facing or customer-facing systems first.
- Business tiers: Apply critical fixes within days, while less urgent systems follow a monthly cycle.
With Microsoft Defender Vulnerability Management, security teams can view threat intelligence, exposure scores, and device-level risk insights in real time. The platform helps prioritize patches based on real-world exploitation data and integrates directly with remediation workflows in Microsoft Intune.
Summary: prioritizing by risk ensures limited IT resources are spent where they matter most. Microsoft security licensing (such as E5 Security) provides the telemetry and automation to support this approach.
3. Test Before Production Deployment
Skipping testing is one of the fastest ways to turn patching into outages. Applying updates without validation risks breaking applications, integrations, or workflows that the business depends on. To reduce this risk, every patching schedule should include a structured testing process:
- Maintaining a test environment that mirrors production.
- Validating patches against core apps and integrations.
- Documenting rollback procedures for quick recovery.
Microsoft 365 offers tools that allow organizations to create pilot groups and staged deployments automatically. You can test patches on a small, low-risk device cohort, evaluate stability, and then deploy across your entire environment.
Summary: testing patches first prevents downtime while keeping security intact.
4. Define Consistent Maintenance Windows
Predictability reduces disruption. Microsoft’s well-known Patch Tuesday is a widely adopted model because it provides consistency for planning and execution.
Following the same principle, IT teams should define clear maintenance windows that set expectations and prevent last-minute surprises:
- Align with vendor release cycles.
- Be communicated early so business units can prepare.
- Roll out in phases, starting with low-risk systems before moving to production.
Summary: consistent maintenance windows keep patching predictable and business-friendly.
5. Verify and Report After Every Cycle
Patching doesn’t end with deployment. The IBM Cost of a Data Breach Report 2025 found that the global average cost of a data breach is USD 4.44 million, while U.S. breaches average USD 10.22 million — the highest in the world. Organizations with strong detection and reporting practices were able to shorten breach lifecycles, reducing costs significantly.
Data: IBM 2025 Cost of a Data Breach Report.
Verification should include:
- Running scans to confirm vulnerabilities are resolved.
- Reviewing logs and metrics for performance issues.
- Generating audit-ready reports for compliance.
Summary: verification and reporting close the loop, proving that patching strengthened security.
Microsoft 365 Intune, Defender for Endpoint, and Purview can provide patch compliance and vulnerability remediation information, meeting the needs of HIPAA, GDPR, or NIST-aligned frameworks.
Put Your Patching Schedule Into Practice

A defined patching schedule is what separates organizations that scramble after outages from those that prevent them entirely. The five best practices — inventory, prioritization, testing, maintenance windows, and verification — turn patching into a safeguard instead of a gamble.
If your team struggles to keep pace, GCS can help build a patching program that keeps your systems secure, compliant, and always online.
——————————————————
Frequently Asked Questions about Patching Schedule Best Practices
Q: What are the five patching schedule best practices?
A: The five best practices are:
- Keep a real-time inventory of all assets.
- Prioritize patches based on risk.
- Test patches before deployment.
- Set consistent maintenance windows.
- Verify and report after every cycle.
Q: How often should IT teams patch systems?
A: Critical vulnerabilities, especially on internet-facing systems, should be patched within days. Lower-risk systems are often patched monthly, usually in line with Microsoft’s Patch Tuesday cycle.
Q: Why is patch testing important?
A: Testing patches in a staging environment prevents outages, since untested updates can break applications, integrations, or workflows.
Q: What happens if patches are missed?
A: Missed patches are one of the main ways attackers break in. Gartner reports that 99% of exploited vulnerabilities are already known at the time of attack, meaning most breaches can be prevented with consistent patching.




