Choosing between Microsoft Defender for Business and Defender for Endpoint comes down to more than licensing. While both offer similar threat protection at the core, they’re built for different environments—with significant differences in visibility, automation, and integration.
If you’re evaluating Microsoft Defender for Business vs Defender for Endpoint, this comparison focuses on what matters in practice: how each tool performs, what it lets you control, and how it fits into a modern security strategy.
What is Microsoft Defender for Business?
Microsoft Defender for Business (MDB) is a streamlined endpoint security product designed for organizations using Microsoft 365 Business Premium. It includes core protections like EDR (Endpoint Detection and Response), attack surface reduction, vulnerability management, and automated remediation.
While MDB provides a foundation for endpoint security, it’s limited in visibility, control, and integration compared to Defender for Endpoint. It lacks key capabilities like custom detection rules, advanced threat hunting, and seamless integration with Microsoft Sentinel or other XDR tools.
For organizations with basic security needs or very limited infrastructure, MDB can be a starting point. But in most cases, especially when regulatory standards or layered protections are required, Defender for Endpoint is the version that enables full-scale security operations.
What is Microsoft Defender for Endpoint?
Microsoft Defender for Endpoint (MDE) is Microsoft’s full-featured endpoint security platform for mid-sized and large organizations. It includes everything in MDB, plus advanced capabilities like threat hunting, custom detection rules, deep API access, SIEM integration, threat intelligence, and centralized incident response across the Microsoft 365 Defender suite.
MDE integrates natively with tools like Sentinel, Purview, and Defender for Identity—making it the go-to choice for organizations with dedicated security operations or compliance requirements.
If your team needs to investigate threats across thousands of endpoints, integrate with SOC workflows, or enforce zero trust policies across devices, MDE is the toolset you’re looking for.
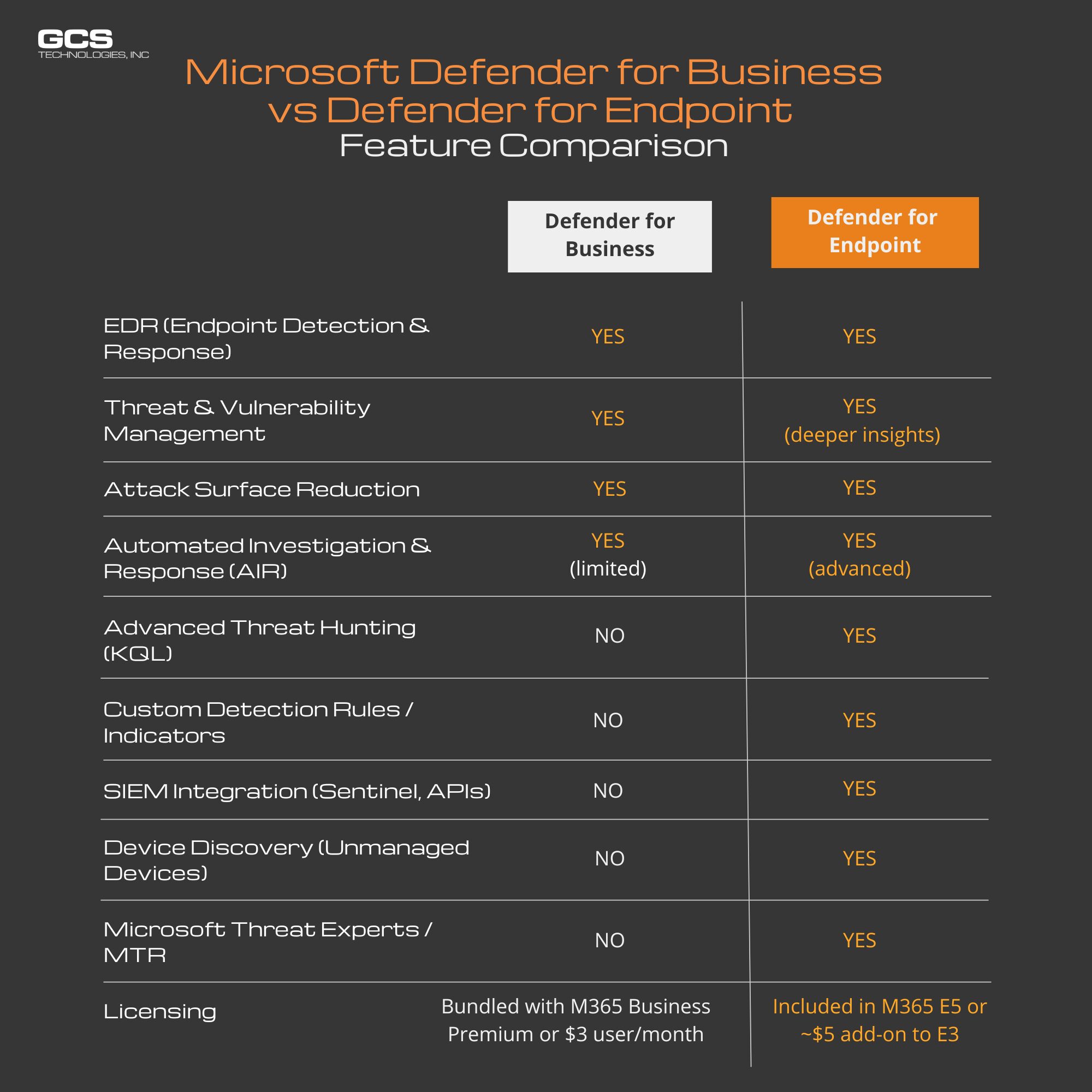
Microsoft Defender for Business vs Defender for Endpoint Feature Comparison
So how do these two solutions compare in practice? In the Microsoft Defender for Business vs Defender for Endpoint debate, both tools share the same core detection engine—but their capabilities, customization, and scalability are very different. Below is a side-by-side breakdown of the features that matter most when evaluating endpoint protection for modern IT environments.
Many people still confuse these with Windows Defender — the basic antivirus built into Windows. Here’s the difference.
5 Real-World Use Case Scenarios
When you move beyond the datasheet and into real environments, the differences between Microsoft Defender for Business vs Defender for Endpoint become impossible to ignore. Here’s how the two solutions compare in actual day-to-day operations—where decisions about alert management, threat response, and integration can directly impact security outcomes and team efficiency.
1. Alert Management and Noise Filtering

- MDB minimizes alerts to avoid overwhelming generalist teams — but this also means limited visibility into early-stage threats.
- MDE captures low, medium, and high-severity events, with full behavioral context and investigation options.
For any organization relying on alert correlation, escalation, and tuning — including small teams working with managed partners — MDE provides the necessary depth.
2. Threat Hunting and Investigation
- MDB lacks threat hunting, limiting your ability to investigate suspicious activity across your environment.
- MDE gives you access to advanced hunting with Kusto Query Language (KQL) and incident timeline views. You can pivot across device logs, correlate with user behavior, and identify lateral movement in multi-stage attacks.
MDE turns your alerts into actionable investigations. MDB assumes you don’t have time to dig deep.
3. Automated Response
- While both solutions support automated remediation, MDB offers only basic actions.
- MDE enables fully customized playbooks, role-based actions, and integration with tools like Microsoft Sentinel and Logic Apps.
This level of automation is critical to enforcing Zero Trust, responding at scale, and adapting to evolving threats — no matter the size of your environment.
4. Unmanaged Device Visibility
- MDE includes passive network device discovery. That means it can spot unmanaged endpoints joining your network—even if they’re not enrolled in Intune or Azure AD.
- MDB has no native support for unmanaged device discovery. If a device isn’t onboarded, it’s invisible.
This matters if you’re trying to reduce shadow IT or enforce compliance across BYOD environments.
5. Integration with the Microsoft Security Stack
MDE is built to integrate across the full Microsoft Defender XDR ecosystem:
- Defender for Identity (DC-level signal collection)
- Defender for Office 365 (phishing, BEC, spoofing)
- Microsoft Sentinel (SIEM)
- Microsoft Purview (DLP)
- Entra ID / Conditional Access
MDB integrates with Intune and Azure AD but lacks the deep connectors needed for enterprise security workflows.
If your company is moving toward a consolidated Microsoft security architecture, MDE is the only version that scales with it.
Why GCS Recommends Defender for Endpoint
Defender for Endpoint gives organizations the visibility, control, and integration needed to maintain strong, consistent protection — whether managing a handful of users or thousands. It supports advanced detection rules, custom alert tuning, and rich incident data, enabling a security strategy that’s both effective and adaptable.
It integrates deeply with the broader Microsoft security ecosystem, including Sentinel, Defender for Identity, and Conditional Access, connecting data across users, devices, and cloud services. This unified view helps eliminate blind spots and supports faster, more informed responses.
- Want to understand how Microsoft’s broader security platform fits into this picture? Read more: What Microsoft Defender XDR’s Achievement Means for Your Protection
Let’s Get You Set Up Right
Whether you’re a small team looking to tighten your defenses or a larger org preparing for compliance audits, we’ll make sure your Microsoft security stack does the job.
Contact GCS to implement Defender for Endpoint with the configurations and coverage that match your team’s real-world needs, without overspending or missing critical protections.



