Phishing is a technique commonly used in malware attacks. In a phishing attack, the attacker sends an email that appears to be from a trusted source, such as a friend or company. The email contains a link or attachment that will install malware on the victim’s computer. Malware can damage or steal your data, and can even take over your computer to use it for criminal purposes.
In this article, we’ll discuss six common techniques used in phishing attacks. Knowing what these techniques are can help you protect yourself and your business from malware infections. The 6 malware techniques commonly used in PHISH attack campaigns are:
- Credential Harvesting
- Malware Attachments
- Link in Attachment
- Link to Malware
- Drive-by URL
- OAuth Consent Grant
Here we walk through an explanation and example of each of the techniques.
Credential Harvesting
Attack technique goal -Target supplies username and password.
In this type of technique, a malicious actor creates a message, with a URL in the message. When the target clicks on the URL within the message, they are taken to a website, the website often shows input boxes for luring the target to submit their username and password. Typically, the page attempting to lure the target will be themed to represent a well-known website to build trust in the target.
Simulation steps:
Step 1: User opens the email payload
Step 2: User clicks the link in email payload
Step 3: User enters credentials in form on website
Credential Harvesting example:
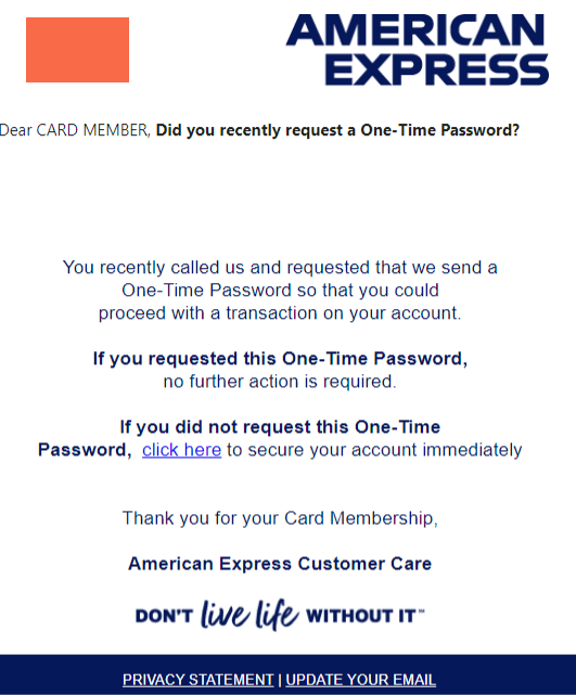
Malware Attachments
Attack technique goal – Target opens attachment.
In this technique, a malicious actor creates a message, with an attachment added to the message. When the target opens the attachment, typically some arbitrary code such as a macro will execute in order to help the attacker install additional code on a target’s device, or further entrench themselves.
Simulation steps
Step 1: User opens the email payload
Step 2: User opens the attachment in the email
Step 3: Code runs from within attachment
Malware Attachment example:
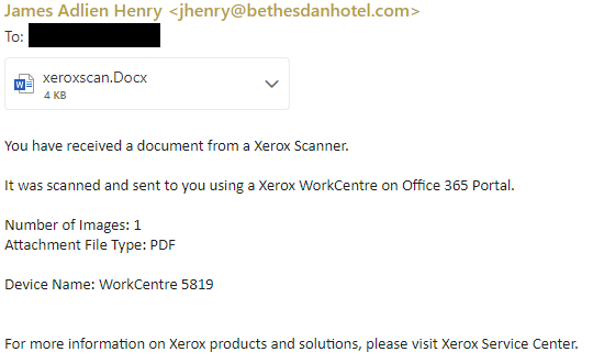
Link In Attachment
Attack technique goal – Target opens attachment.
In this technique, which is a hybrid of a Credential Harvest, a malicious actor creates a message with a URL in an attachment, and then inserts the attachment into the message. When the target opens the attachment, they are represented with a URL in the actual attachment. If the target then clicks on that URL they are taken to a web site, the website often shows input boxes for luring the target to submit their username and password. Typically, the page attempting to lure the target will be themed to represent a well-known web page to build trust in the target.
Simulation steps
Step 1: User opens the email payload
Step 2: User clicks the URL in the attachment
Step 3: User enters credentials in form on website
Link In Attachment example:
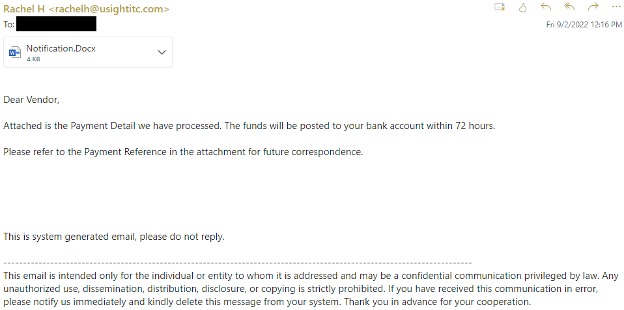
Link to Malware
Attack technique goal – Target opens attachment.
With this technique, a malicious actor creates a message, with an attachment added to the message. However, instead of directly inserting the attachment into the message, the malicious actor will host the attachment on a well-known file sharing site, (such as SharePoint, or Dropbox) and insert the URL to the attachment file path into the message. When the target clicks on the URL it will open the attachment, typically some arbitrary code such as a macro will execute in order to help the attacker install additional code on a target’s device, or further entrench themselves.
Simulation steps
Step 1: User opens the email payload
Step 2: User clicks the URL in the email
Step 3: Code runs from within attachment
Link To Malware example:
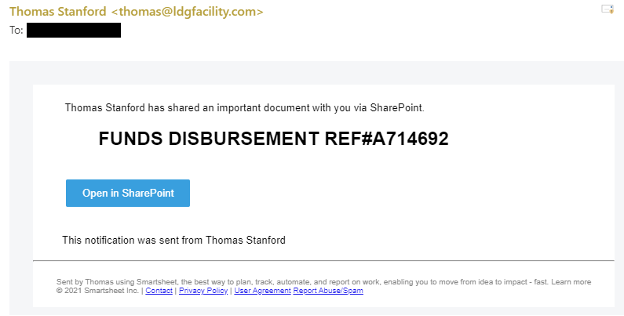
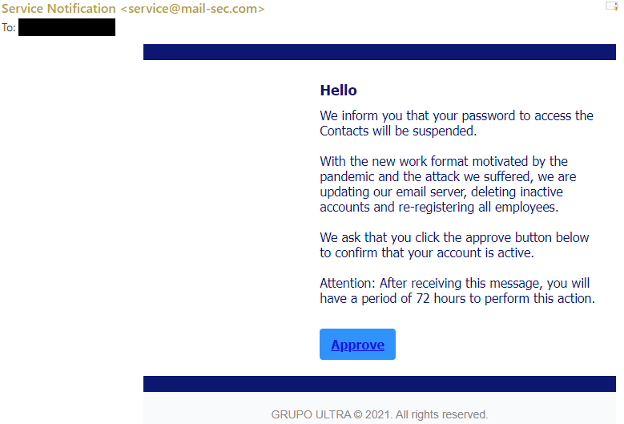
Drive-by URL
Attack technique goal – Target clicks URL.
In this approach, a malicious actor creates a message, with a URL in the message. When the target clicks on the URL within the message, they are taken to a website, the site will then try and run some background code to gather information about the target or deploy arbitrary code to their device. Typically, the website attempting to lure the target will be a well-known website that has been compromised in some fashion, or a clone of a well-known website itself. This familiarity with the website builds trust in the target that it is safe to click, this is also sometimes known as a watering hole technique.
Simulation steps
Step 1: User opens the email payload
Step 2: User clicks the URL in the email
Step 3: Code runs from site the URL is hosted on
Drive-by URL example:
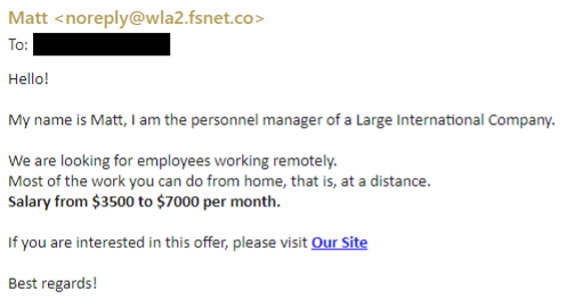
OAuth Consent Grant
Attack technique goal – Target grants permissions.
When this technique is used, a malicious actor has created an Azure Application that asks the target to grant the application permissions over some of the target’s data. The application will provide a URL that is sent to the target by malicious actor along the similar lines of a credential harvest technique, as a URL in a message. This time, clicking on the URL will activate the applications consent grant mechanism, displaying a message such as “Contoso App, would like read access to your inbox” please click the button to approve or deny the request.
Simulation steps
Step 1: User opens the email payload
Step 2: User clicks the URL in the email
Step 3: User clicks and grants permission
OAuth Consent Grant example:
The Importance of Understanding Phishing techniques
Phishing is the most common technique used by malware attackers because of its effectiveness. However, with some simple steps you can protect yourself from these attacks. First, make sure you know how to identify phishing emails. Look for warning signs like poor grammar or mismatched fonts. Second, never click on links or attachments in suspicious emails. Finally, keep your antivirus software up-to-date and use strong passwords to protect your accounts. By following these tips, you can help keep yourself and your team safe from malware attacks.
